@shivamycodee/confession
11th September 2024
Why you need this package?
I have created a simple react vite webiste & node.js server to expalin the usage...
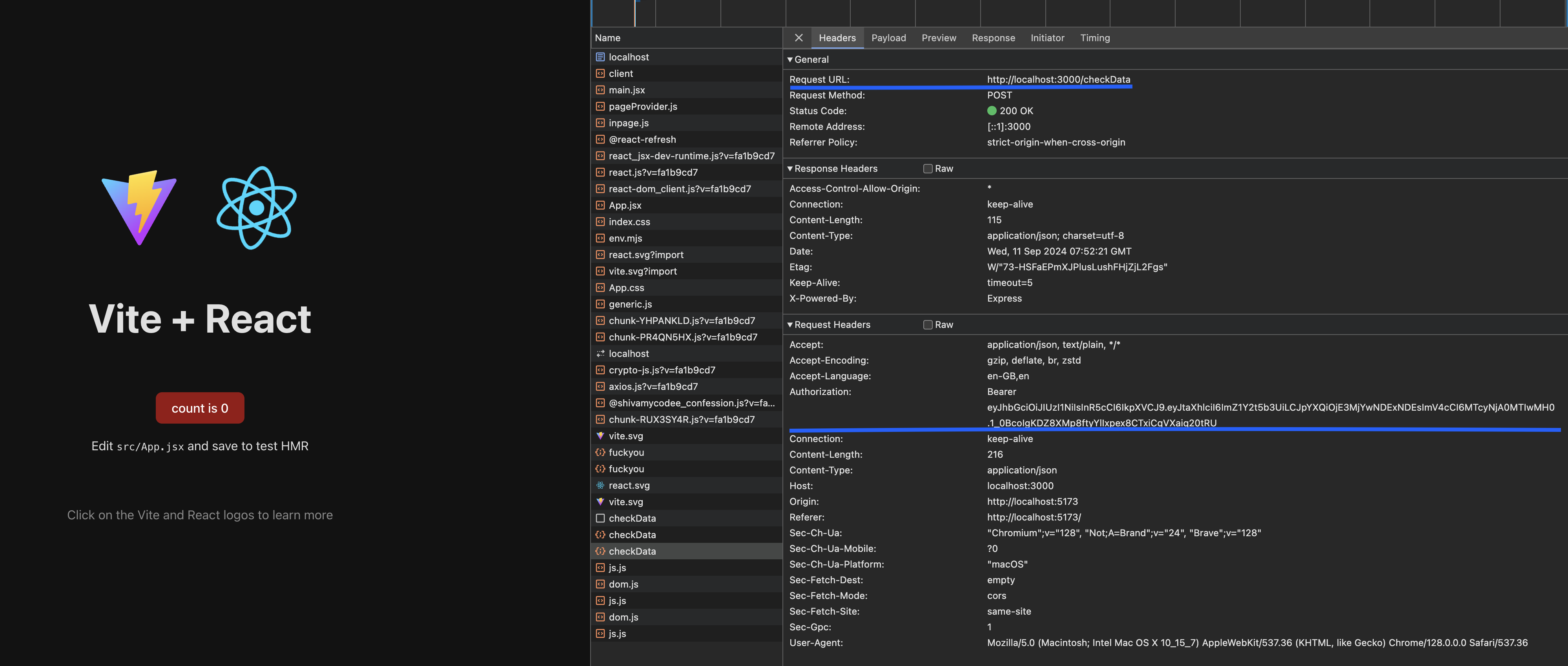
- As you can see in the image below i'm running my webiste, which is sending a post request to the server at endpoint checkData, i'm sending a JWT Bearer token and encrypted payload with my request.
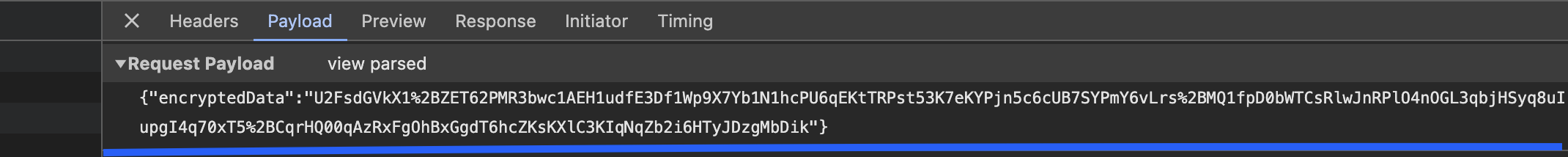
- The issue with the current procedure I followed (and many others do as well) is that I assumed using JWTs with short expiration times (mine is 30 seconds) and sending encrypted payloads would be enough to protect my server from replay attacks, DoS attacks, DDoS attacks, etc. However, it is not. In the image below, I demonstrate a replay attack using a third-party tool, Postman Desktop, and I was able to easily fetch and manipulate my data by simply taking the JWT (before it expired) and the encrypted payload, then entering them into Postman.
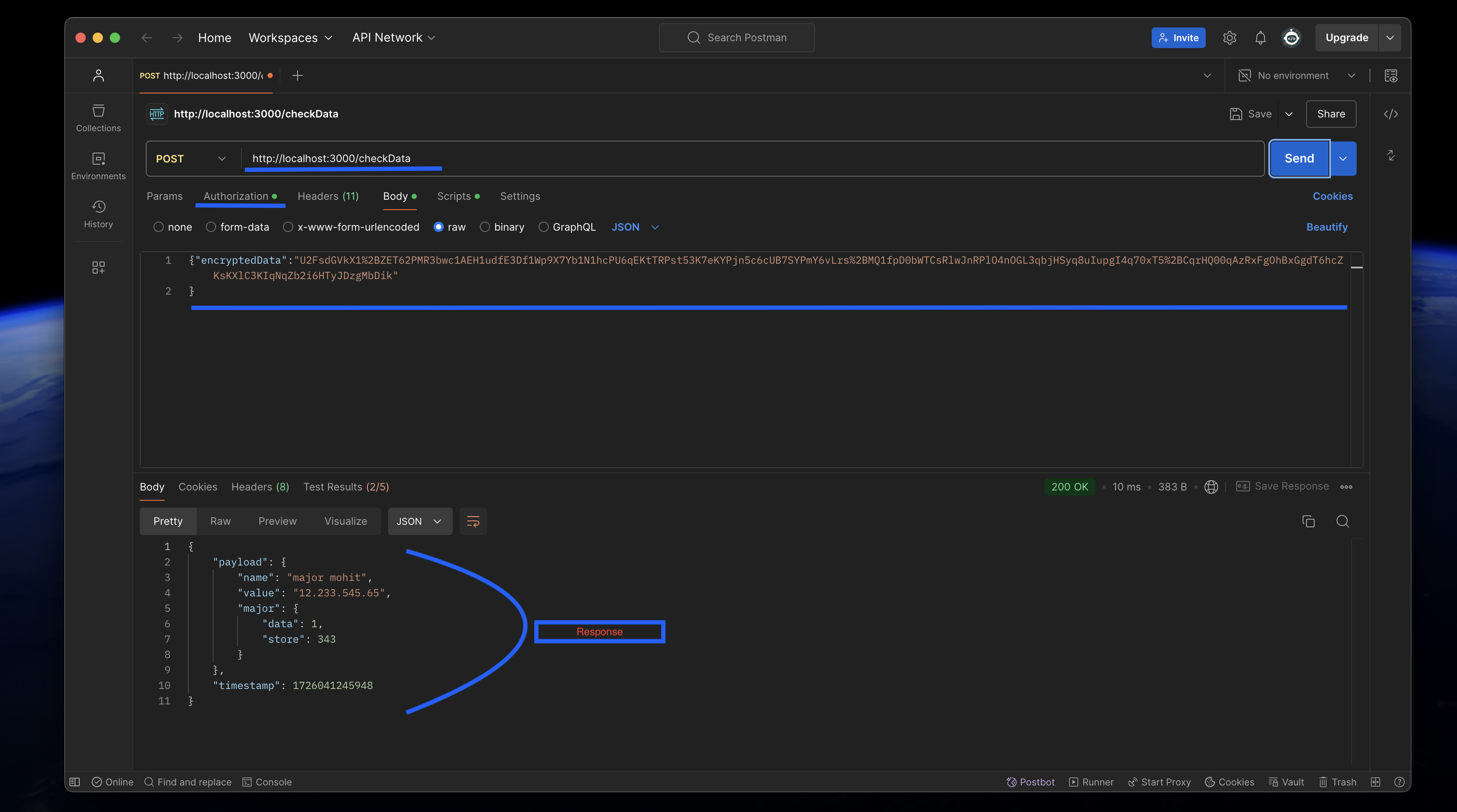 Now you might say, 'But what if I keep the expiration time of my JWT very short, like just a few seconds? Although the client would need to request it multiple times, the hacker wouldn’t be able to do anything, right?' Wrong. Your JWT endpoint would still be open for anyone to call, so a hacker could simply request a new JWT and use the old encrypted payload to access the data.
Now you might say, 'But what if I keep the expiration time of my JWT very short, like just a few seconds? Although the client would need to request it multiple times, the hacker wouldn’t be able to do anything, right?' Wrong. Your JWT endpoint would still be open for anyone to call, so a hacker could simply request a new JWT and use the old encrypted payload to access the data.
My package, @shivamycodee/confession, resolves this issue. It uses Bun to make it optimized and fast, checkout this tweet to get a simple comparison
How package handles this issue?
My package uses the encrypted payload as a key to differentiate between requests, and I have added a nonce to the encrypted payload to keep track of each request. I store every request in a cache folder with a timestamp. The request will be removed from the server after the JWT expiration time. For example, if the JWT expiration time is 30 seconds, any request hash older than 30 seconds will be removed from the server. So, if a hacker attempts a replay attack using a valid JWT and encrypted payload, this is the response from my package. But what if the hacker uses a valid JWT and an old encrypted payload that has been removed from the server cache? Don’t worry—those cases are also handled by my package. Below, I have demonstrated various attacks and the responses from my package.HERE THE HACKER I'M REFEREING TO CAN BY A THIRD PARTY BETWEEN CLIENT AND SERVER OR THE CLIENT HIMSELF.
- When hacker tries to do a replay attack using a valid JWT and encrypted payload, this would be the response from my package:
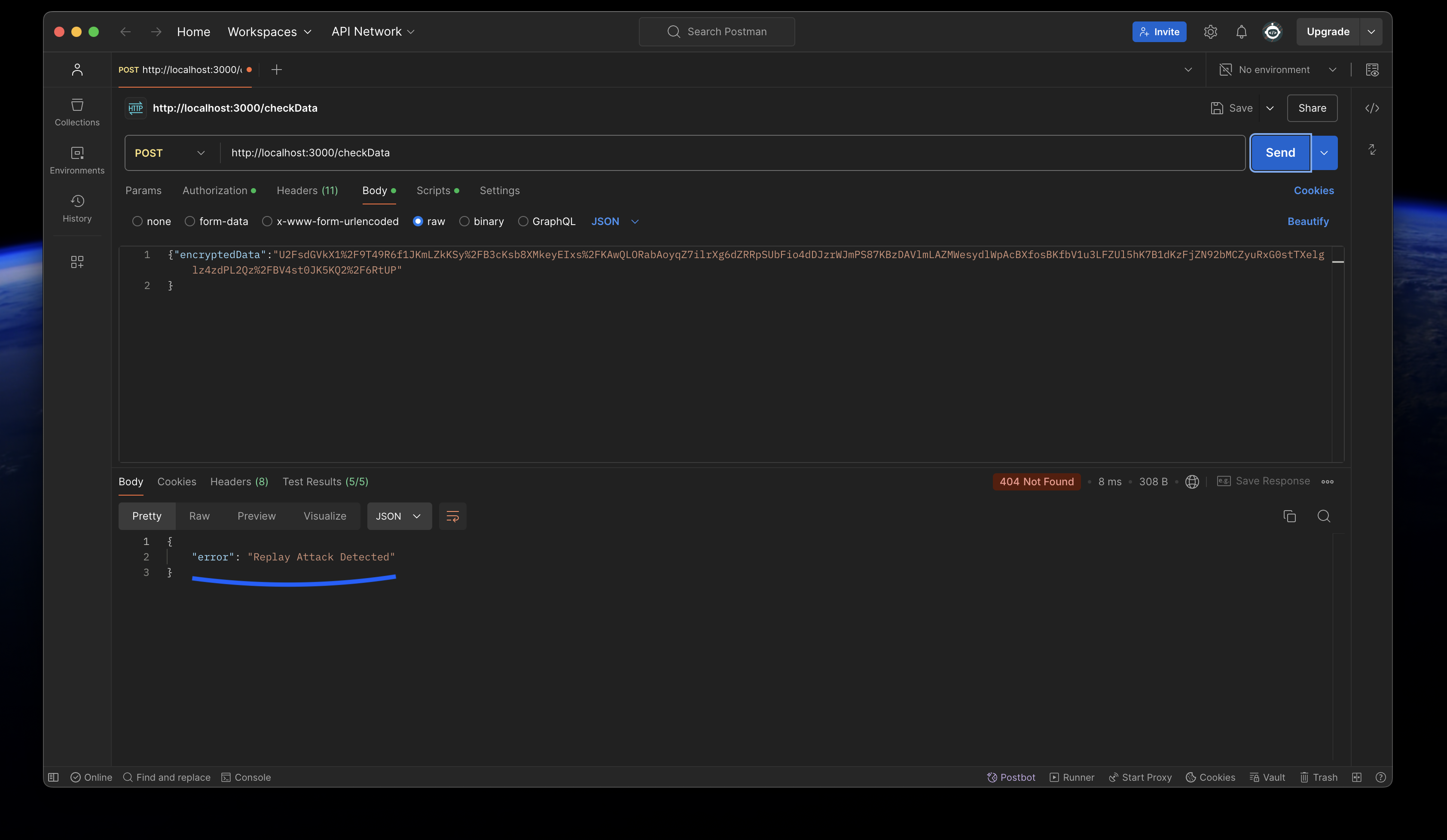 "Replay attack detected" would be returned to the request.
"Replay attack detected" would be returned to the request. - When hacker tries to do a replay attack using an expired JWT and encrypted payload, this would be the response from my package:
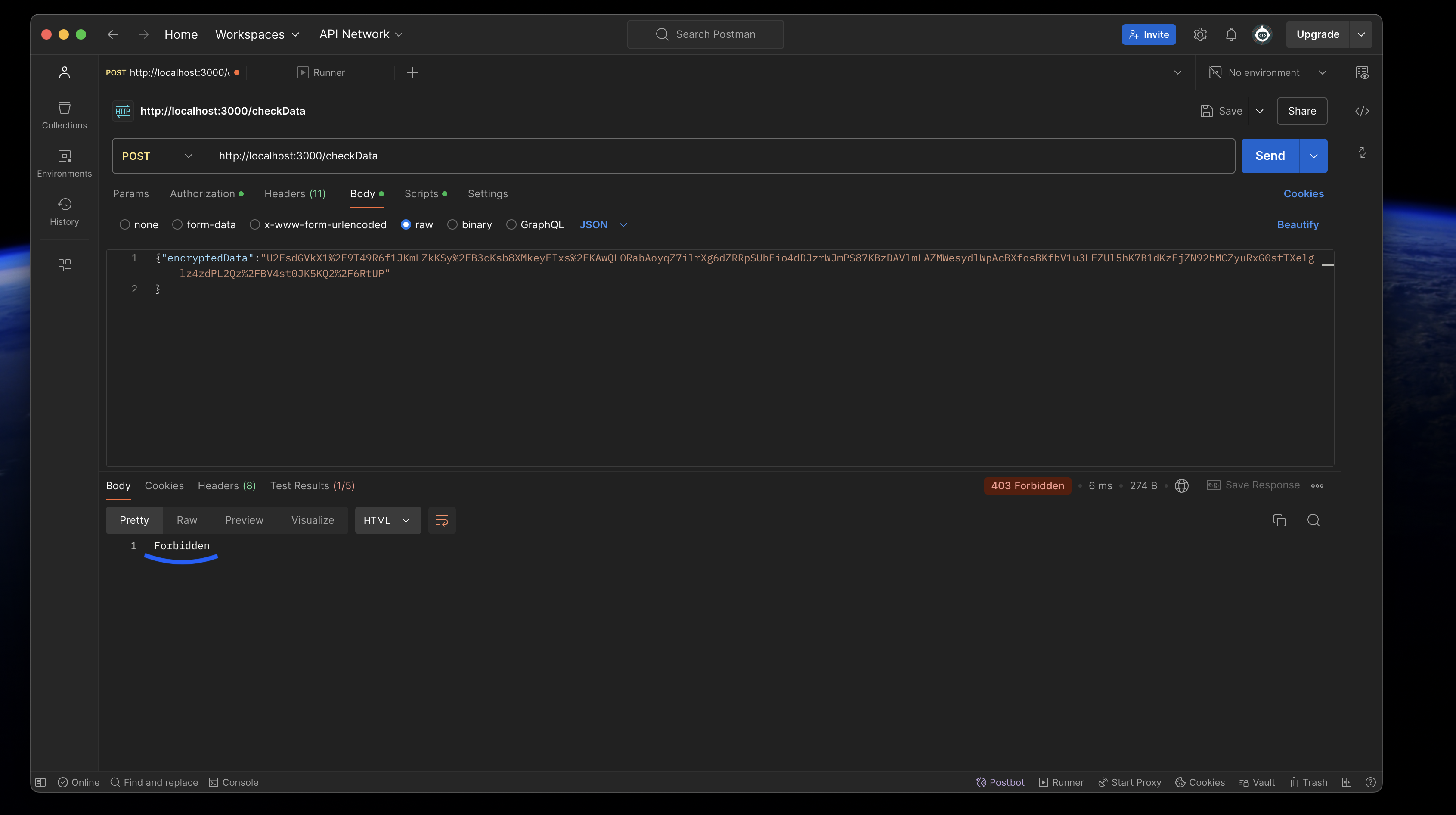
- When hacker tries to do a replay attack using a valid JWT and an OLD encrypted payload which is removed from the server cache, this would be the response from my package:
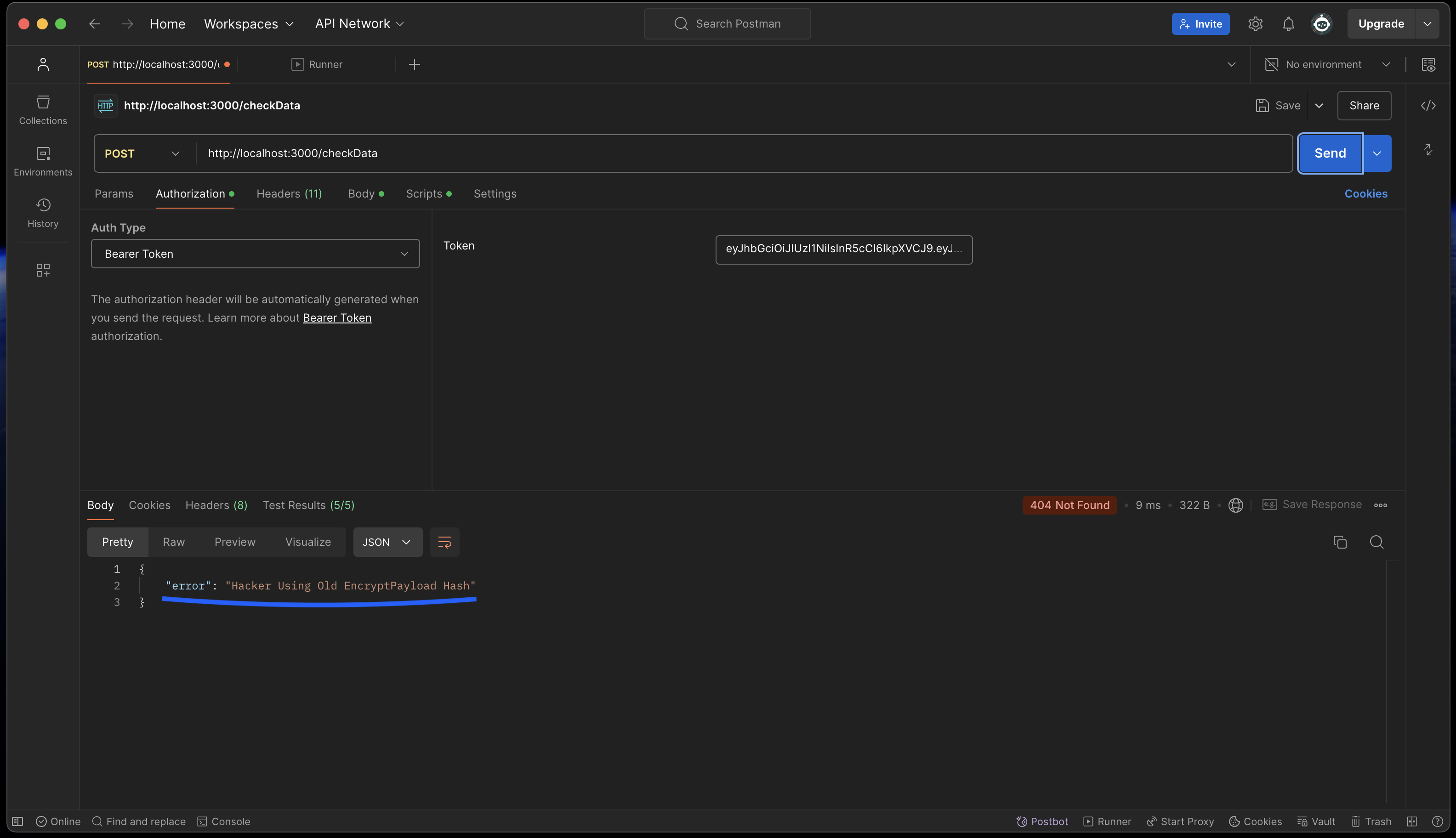 "Hacker using old EncryptedPayload Hash." would be returned to the request.
"Hacker using old EncryptedPayload Hash." would be returned to the request.
Here is a simple chart to explain how my package handles request...
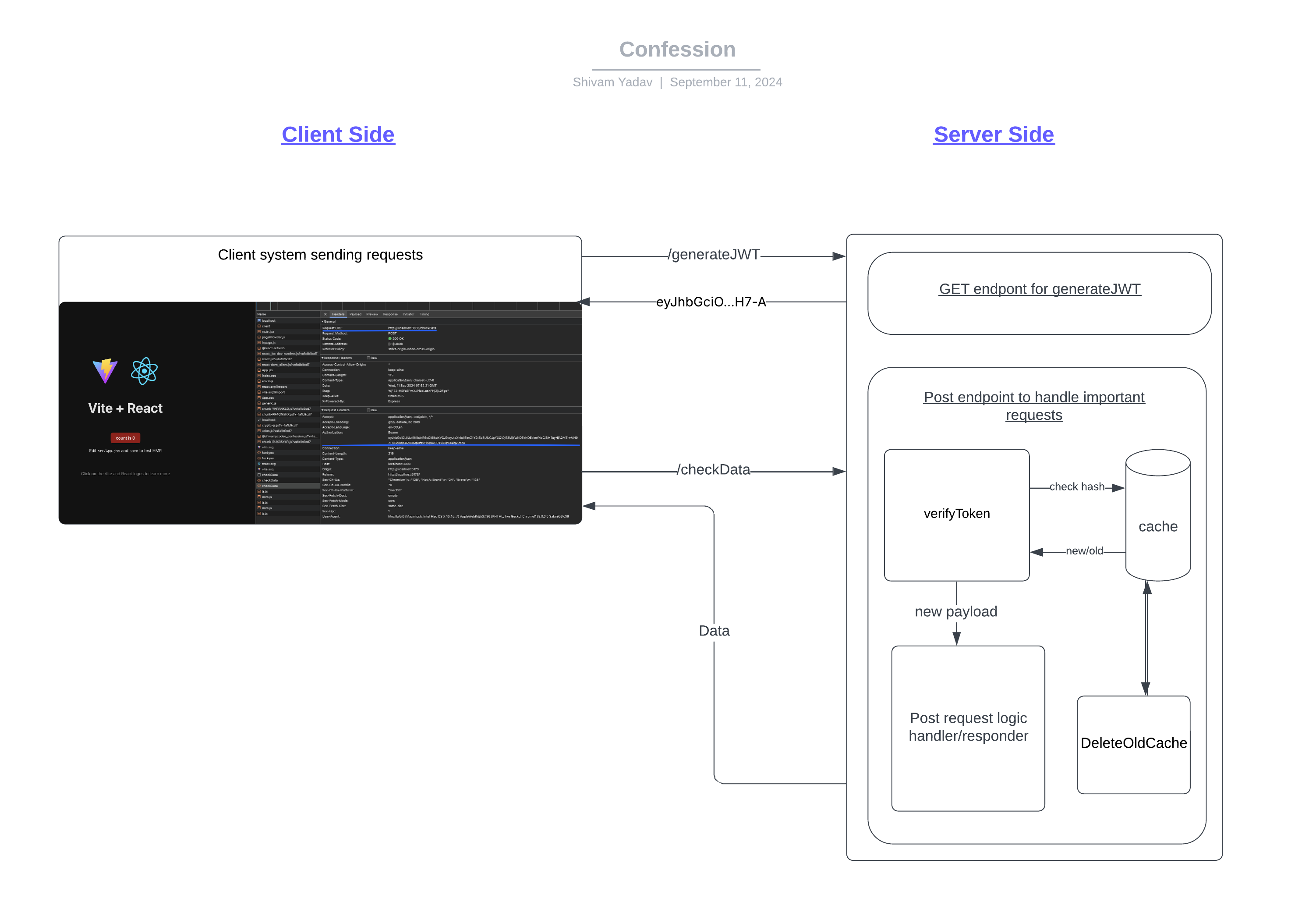
If you find any problem/issue in my package, please create an issue thread here.
If you are interested in this idea, hit me up at twitter/linkedin/telegram , links are in About Me Section.